Share this
Importance of an End-to-End IT Security Framework for a Cloud-Enabled Digital Enterprise
Author: Ian Black, Technical Solution Manager
During the past two years, it was the cloud that enabled organizations across the world to accelerate the pace of digital transformation (DX) initiatives. Cloud has been the foundation of distributed enterprise functions, workplaces, workloads, and supply chains. It has driven business model innovation and boosted efficiency and agility, leading to resilient, sustainable business growth.
Qatar has been no exception to this growth. Public and private sector entities in the country have been reporting notable progress on their DX journeys. A recent IDC study showed that 64% of organizations in Qatar have brought forward their DX initiatives by one or two years. The Qatari government, which has adopted a cloud-first approach, has been an ideal role model. The cloud-first approach of the government has also triggered the in-country datacenter investments of hyperscale cloud providers. Such developments are encouraging investments by local cloud solution providers, accelerating the migration of IT workloads to a cloud environment.
According to IDC‘s CIO survey conducted in early 2021, 38% of organizations in Qatar are prioritizing the use of public and private cloud to create hybrid cloud environments. The shift to hybrid cloud is poised to accelerate as the local regulatory environment and policies mature.

Securing the Hybrid Cloud Architecture
It’s clear that core-to-edge DX is progressing at a rapid pace in Qatar. However, securing the digital assets of an organization, whether on premises or in the cloud, is a necessity. The threat landscape is continuously evolving, with the tempo and sophistication of attacks increasing. Successful cyberattacks can disrupt business operations, cause data loss, and lead to reputational damage and financial loss.
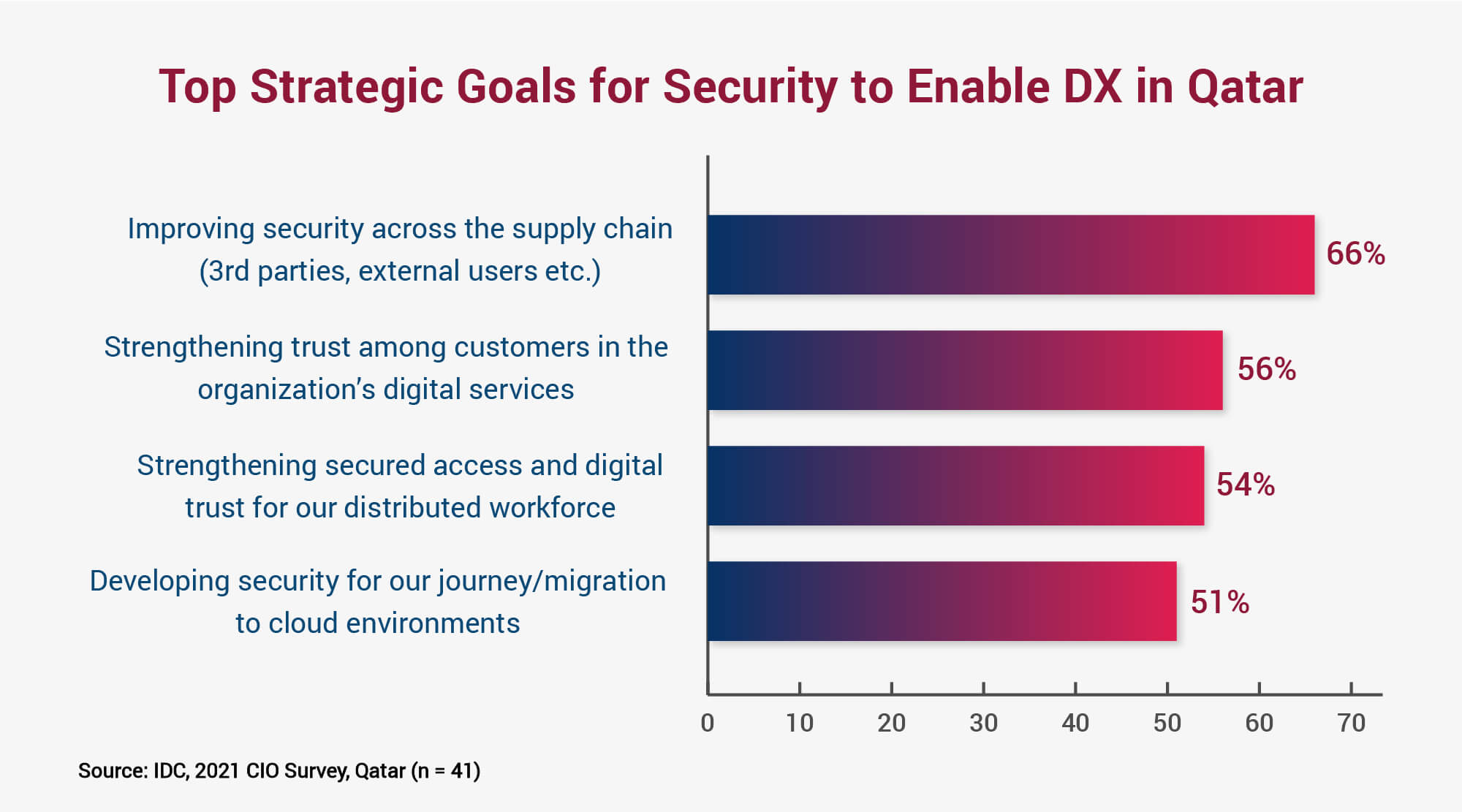
The good thing is that most organizations in Qatar have prioritized IT security as a strategic element of their cloud-enabled DX journeys (this was occurring even before the COVID-19 pandemic). They are embracing a proactive approach — primarily to improve security across the distributed functions and digital supply chain. The digital supply chain is the bridge between the supplier, organization, and the customer. It is key to any organization’s future relevance.
Other key priority areas for organizations are strengthening customer trust in their digital services, securing access for the distributed workforce, and implementing an end-to-end security framework for the hybrid cloud architecture.
Facing the Challenges to Enable a Resilient Business
Countering the growing speed and scale of AI- and automation-driven cyberattacks is a challenge faced by all organizations. Ransomware attacks are among the most frequently encountered cyberattacks in Qatar. Attackers are seeking to take over business-critical functions and cause business disruptions.
Other security challenges include meeting regulatory requirements, updating security policies, and applying consistent security controls across the on-premises and cloud elements of a hybrid architecture.
Improve Your Cloud Security Posture with a Holistic Approach
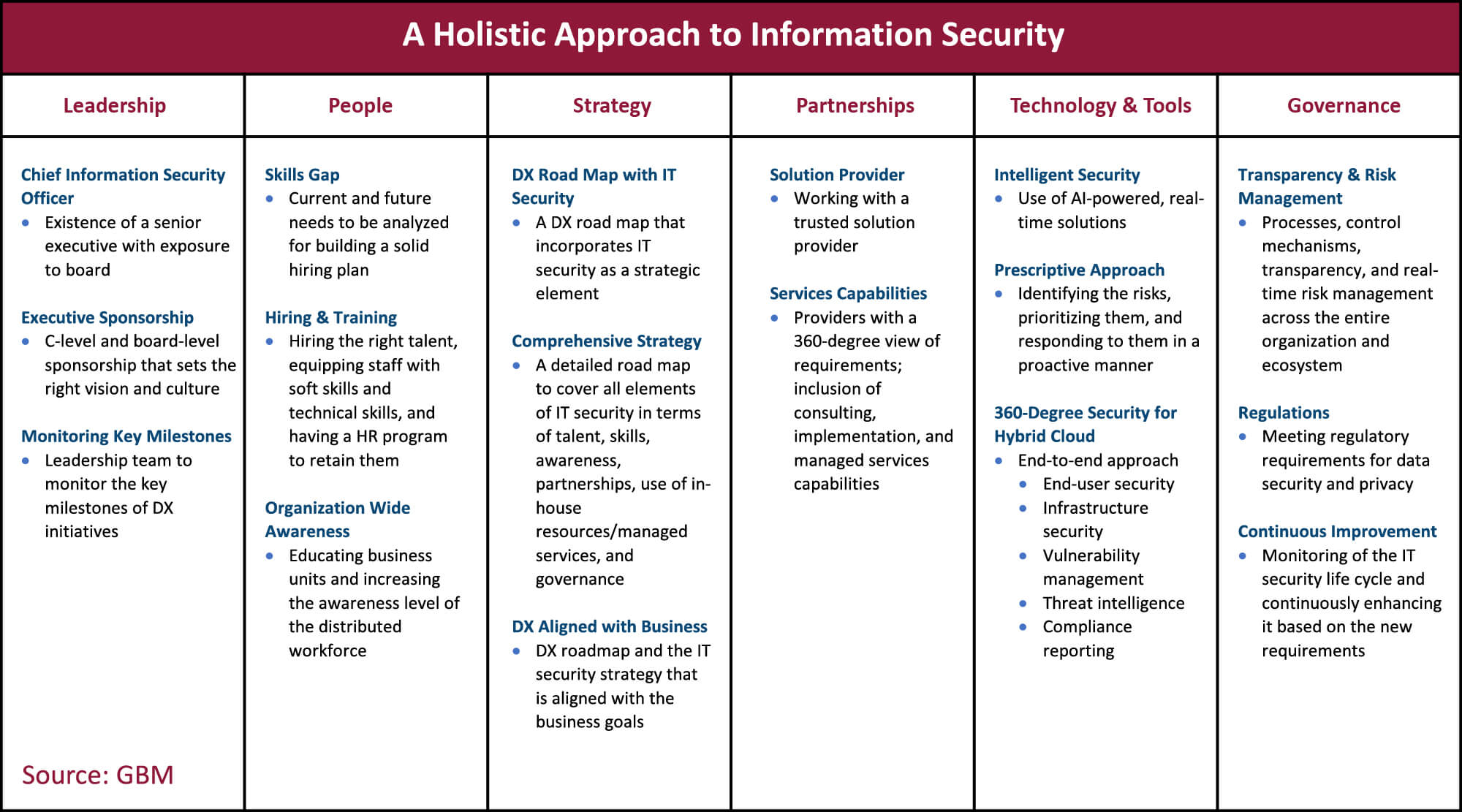
Addressing these challenges requires a structured and organization-wide approach to IT security. Leadership, People, Strategy, Partnerships, Technology & Tools, and Governance are the foundational pillars of an end-to-end, sustainable IT security framework.
The table below provides a detailed view of the best practices for each of these aspects. A lack of focus in any one of them will slow organizational DX and increase risk exposure.
Partnerships to Take You Forward
Meeting today’s security challenges requires a holistic approach to IT security. Such an approach should be a strategic part of your DX road map. Success depends on collaborating with trusted partners that have a proven track record in hybrid cloud architecture and who can work as an extension of your team. These partners should have the capability to provide consulting, implementation, and managed services to address the evolving needs of your organization.
Solution providers should deliver best-in-class security solutions with built-in AI, real-time monitoring, prediction, and prescriptive analytics capabilities. This will help you build a resilient hybrid cloud architecture and drive sustainable business growth.
Our team at GBM and IBM have the expertise across the full range of digital transformation and cloud security solutions. IBM offers comprehensive Identity and Access Management solutions from single and trusted source. Their end-to-end security solutions in the areas of strategy and risk management, digital trust, threat management and cloud security will help you align your security strategy with your business. To find out more on how GBM and IBM can help you accelerate your transformation visit: https://www.ibm.com/security/solutions
